
Threat intelligence is an integral part of security operations. With it, you can gain a deeper understanding of emerging threats and make sure you’re one step ahead of them.
But this can’t be done without powerful, data-driven solutions. SOC specialists desperately need them for better monitoring, triage, and reaction to threats.
Thanks to services like ANY.RUN’s TI Lookup, threat intelligence supports SOC efficiency in several ways. Here are three practical real-world examples:
Faster Alert Triage
TI Lookup contains Indicators of Compromise (IOCs), Behavior (IOBs), and Attack (IOAs) of active cyber threats targeting 15,000 organizations worldwide. The data comes from sandbox analyses of the latest malware and phishing samples performed by 500,000 security professionals in ANY.RUN’s Interactive Sandbox. Then it undergoes pre-processing and enriches TI Lookup every two hours.
How can this help accelerate alert triage? It’s very simple: you can browse accumulated threat intelligence to find accurate and fast answers required for further decision-making.
Once you get an alert containing a suspicious indicator or an artifact , all you need to do is to look it up in the database to:
- Detect if it’s actually malicious
- If yes, identify its threat name, as well as associated IOCs, IOAs, and IOBs
- See the scope of the attack
For instance, with a query like this, we can determine whether a domain is malicious or not:
Upon entering it, it takes seconds to see the conclusion: yes, it’s associated with malware. More precisely, with Lumma, an information stealer targeting cryptocurrency wallets, credentials, and other sensitive data.
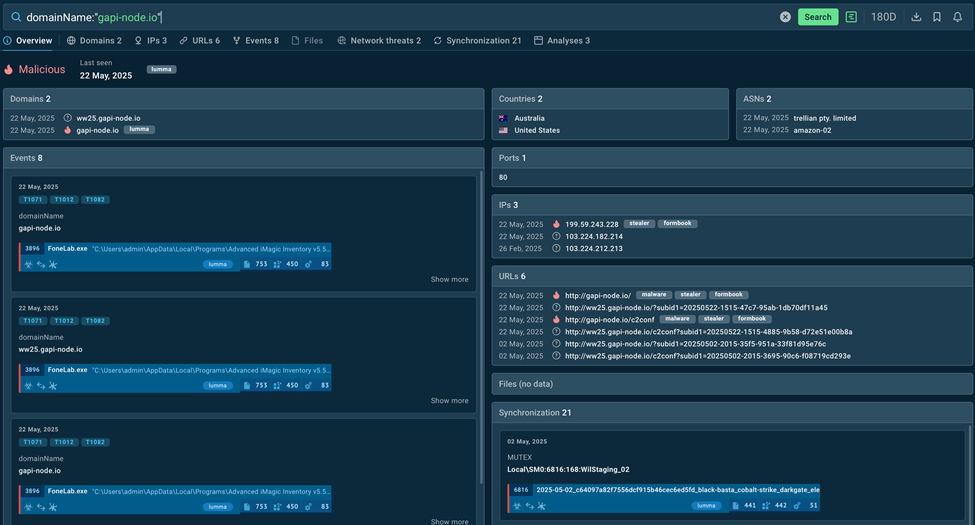
Search results in TI Lookup
You can see the scope of the threat (8 events are associated with the domain at the moment of writing), as well as related IPs and URLs.
All this info was received with the help of a simple query that took seconds to provide you with everything you need to know—that’s how TI Lookup speeds up the alert triage.
For further monitoring, you can also subscribe to the query threat by clicking the bell icon in the top right corner to get notified about new samples and track the evolution of the attack.
Accelerate your alert triage with 50 trial requests in ANY.RUN’s TI Lookup
Confident Incident Response
After gaining initial info on the threat, your next step should be reacting to the incident it caused. Extensive threat intelligence can once again help you decide what action to take.
Let’s go back to the previous query and scroll down. There you’ll find links to analysis sessions in ANY.RUN’s Interactive Sandbox, which include the domain we’ve just browsed.
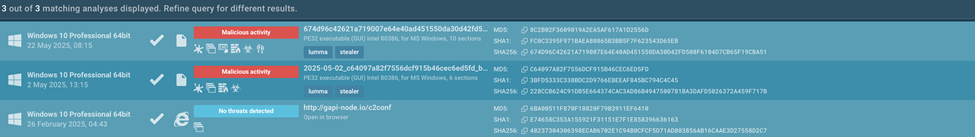
List of analysis sessions related to the threat in TI Lookup
Clicking one of them will take us to the sandbox, a virtual machine for secure malware detonation and analysis. There we can see how the threat unfolds and learn additional details, such as its network activity and TTPs.
Threat intelligence is more than just a list of indicators. It helps you form a fully-fledged picture of the attack. Here’s one of the analyses involving the above-mentioned domain.
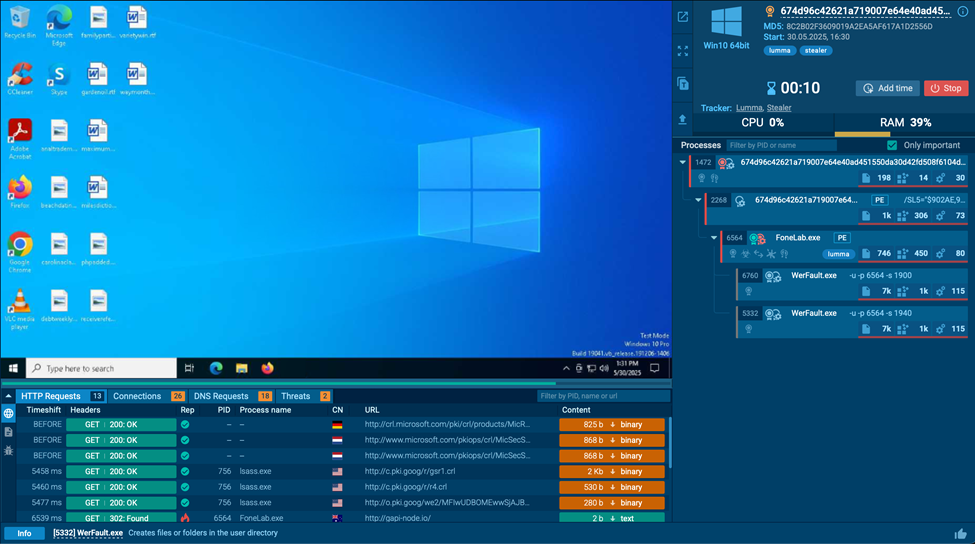
Analysis session in ANY.RUN Sandbox
It takes you to ANY.RUN’s Interactive Sandbox, where you can observe the threat’s entire execution chain to collect extensive info on how it operates on the infected system. The findings can be used to enrich your response efforts and mitigate the incident faster and more effectively.
You can rerun the analysis with different VM settings and manually engage with the threat inside the safe virtual environment to observe how it reacts to your input. For example, you can go to:
- Processes: To see what actions go on in the system because of the threat.
- Network: For info on associated network activities (e.g., HTTP and DNS requests)
- ATT&CK: Learn about the TTPs of the threat via MITRE ATT&CK Matrix.
An in-depth view of the threat will then help you confidently respond to the incident.
Effective Threat Hunting
Last but not least, threat intelligence allows you to act proactively and conduct efficient threat hunting operations.
It takes just one simple search request to check a suspicious line from your PowerShell logs:
The results tell us that it is related to a Stegocampaign. This means that the malware in question relies on steganography, using malicious code injections into image files to spread.
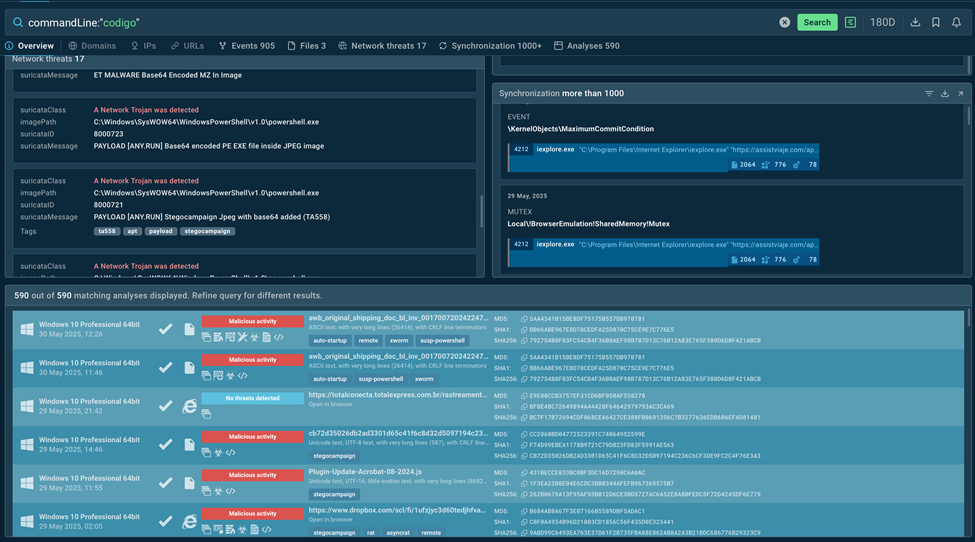
Results of the query in TI Lookup
By continuing your investigation in the sandbox, you can find out extensive details on the threat’s activities. Use them to proactively neutralize it and protect your infrastructure.
Conclusion
Solid threat intelligence solutions not only provide you with data on threats but lead to measurable improvements in daily security tasks. With their help, you can upgrade your threat hunting, achieve a higher level of detection rates, and respond to threats fast and with confidence.
Leave a Reply